In this session, I would like to introduce the process of modifying the WireGuard kernel code to create L2 WireGuard that can operate in a Layer 2 environment and running it on NanoPi. 😎
2. How L2 WireGuard Works
3. L2 WireGuard Operation Test #1
The image below shows an example of remotely accessing a printer (printing directly from home to an office printer) using the mDNS protocol. This is absolutely impossible with a Layer 3 VPN, but it is not the case with a Layer 2 VPN (it is possible).
A long time ago, I made a product with SoftEther VPN, and I'll introduce the drawing I made at that time here. I plan to examine whether a similar configuration is possible with L2 WireGuard, which will be explained in Chapters 2-4. 🔍
2. How L2 WireGuard works
(Personally) I've been using WireGuard for about 7-8 years now. During that time, I've created commercial products based on WireGuard and also worked on changing the protocol.
______________________________
As we all know, WireGuard was designed to operate basically at Layer 3, that is, IPv4/IPv6 layer. In fact, it can handle almost all protocols just by operating at Layer 3 (there is no problem at all in providing services). However, if WireGuard can be made to operate at Layer 2 like OpenVPN (L2 mode) or SoftEther VPN, that would also be quite exciting. 😍
Simple and fast WireGuard, now extended to Layer 2 !
The content introduced in this chapter is about L2 WireGuard, which modifies the WireGuard kernel code to operate on Layer 2, and is based on the content of the site below. Before going into the detailed explanation, I would like to express my gratitude to the original author, Fadis (NAOMASA MATSUBAYASHI) .
a) Basic design direction of L2 WireGuard
In order for WireGuard to operate at layer 2, the following three things must be considered first.
- (1) In order to tunnel the entire Ethernet frame, how can we change the timing of sending the packet from the IP layer to the Ethernet layer?
- When creating a wireguard interface (e.g. wg0), wouldn't it be okay to create it as an ethernet device?
- To use an analogy, you can think of it as making a tun device into a tap device.
- (2) In Ethernet packet communication, there are non-IP packets such as ARP in addition to IP packets. Therefore, what should be done to ensure that non-IP packets such as ARP packets are received in addition to IP packets when receiving packets?
- After decoding and decapsulating the received packets, wouldn't it be possible to modify it to pass through non-IP packets?
- What are some non-IP protocols? ARP, IPX, Appletalk, NETBEUI, VLAN, LACP...
- (3) WireGuard basically performs table lookup(allowed_ips) based on src/dst IP . This is not a problem for IP packets, but it is a problem for non-IP packets. Also, even for IP packets, multicast and broadcast packets are problematic when processed. This part is directly related to the Layer 3 wireguard design idea, and modification is inevitable when switching to the Layer 2 method.
https://slowbootkernelhacks.blogspot.com/2020/09/wireguard-vpn.html
Receive encrypted IP tunnel packet (wg_receive) -> Remove tunnel and decrypt ( decrypt_packet) -> Forward to upper level ( wg_packet_rx_poll )
The wg_packet_rx_poll( ) function takes packets that have already been decrypted (decapsulated) from the queue, processes them appropriately, and then sends them up to the tcp/ip stack using the napi_schedule function. In this process, since the existing code is implemented only for IP packets, non-IP packets such as ARP are excluded from the processing target. Therefore, this needs to be appropriately modified, and the function that needs to be modified is wg_packet_consume_data_done( ) .
- Part that filters IPv4 and IPv6 packets. In other words, part that filters only IPv4 and IPv6 packets.
- The part that attempts an allowedips lookup using the source ip address.
As for the part where allowedips lookup (lookup targeting the source address) is attempted when receiving a packet, since this has already been explained (same concept) in the transmission processing (lookup targeting the destination address), we will focus here on implementing the code to prevent non-IP packets from being filtered. To this end, L2 WireGuard additionally implemented a function to obtain the length of a packet as shown below , and modified the code to prevent non-IP packets from being filtered using this function.
I tried to express the design principles/background of L2 WireGuard in my own way as much as possible, but there are still some awkward parts. 😂 Please read the pdf document written by Fadis to find the missing parts.
In the next chapter, we will verify that the L2 WireGuard implemented in this way really works without any problems using two NanoPis.
In this chapter, we will use one NanoPi R2S Plus and one NanoPi R5C to verify whether L2 WireGuard is operating normally.
I bought a NanoPi R2S Plus and a R5C board from FriendlyElec. The reason is to make L2 WireGuard VPN Routers.
<NanoPi R2S Plus>
https://www.friendlyelec.com/index.php?route=product/product&product_id=296
<NanoPi R5C>
https://www.friendlyelec.com/index.php?route=product/product&product_id=290
<Reasons for choosing NanoPi R2S Plus>
The price is very cheap. $36 including case (but excluding power adapter) => $40 is enough even if you get everything!
It has two Ethernet ports (the WAN port is USB 3.0 based) so it can be used as a Security Gateway.
It is equipped with eMMC (32GB). If the structure boots only with microSD, it may be a security issue.
It has a Wi-Fi chipset (this is optional and costs $9.99 extra).
There is a debug interface (USB 3.0) on the outside of the case.
NanoPi is considerably more stable than other Pi types (there is no problem in commercializing it).
[Figure 3.1] NanoPi R2S Plus(1) - Key Features [Source - Reference 12]
[Figure 3.2] NanoPi R2S Plus(2) - Board top/bottom [Source - Reference 12]
[Figure 3.3] NanoPi R4S Plus(3) - Metal Case [Source - Reference 12]
[Figure 3.4] NanoPi R4S Plus(4) - Network Speed [Source - Reference 12]
a) Build L2 WireGuard
Based on the changes made so far, let's build the kernel again and create the wireguard.ko file.
$ cd friendlywrt23-rk3328
$ cd kernel/drivers/net/wireguard
$ grep -rl L2_WIREGUARD
=> Based on Fadis' code, I modified the file below and processed the L2_WIREGUARD feature to make it easier to distinguish the code.
allowedips.c
📌 Note) Since the IPX-related code is not visible in kernel 6.1.63 used in NanoPi, the IPX-related code in the l2 wireguard code was removed for convenience. It seems that they decided that it is no longer used because it is such an old protocol.
$ cd friendlywrt23-rk3328
$ ./build.sh kernel
For NanoPi, the kernel build is performed like this.
...
CC [M] /mnt/hdd/workspace/mini_devices/friendlywrt23-rk3328/scripts/sd-fuse/out/rtl8812au/hal/phydm/rtl8821a/phy
dm_rtl8821a.o
CC [M] /mnt/hdd/workspace/mini_devices/friendlywrt23-rk3328/scripts/sd-fuse/out/rtl8812au/hal/phydm/halrf/rtl882
1a/halrf_iqk_8821a_ce.o
CC [M] /mnt/hdd/workspace/mini_devices/friendlywrt23-rk3328/scripts/sd-fuse/out/rtl8812au/platform/platform_ops.
o
LD [M] /mnt/hdd/workspace/mini_devices/friendlywrt23-rk3328/scripts/sd-fuse/out/rtl8812au/rtl8812au.o
MODPOST /mnt/hdd/workspace/mini_devices/friendlywrt23-rk3328/scripts/sd-fuse /out/rtl8812au/Module.symvers
CC [M] /mnt/hdd/workspace/mini_devices/friendlywrt23-rk3328/scripts/sd-fuse/out/rtl8812au/rtl8812au.mod.o
LD [M] /mnt/hdd/workspace/mini_devices/friendlywrt23-rk3328/scripts/sd-fuse/out/rtl8812au/rtl8812au.ko
make[1]: Exit directory '/mnt/hdd/workspace/mini_devices/friendlywrt23-rk3328/kernel'
'rtl8812au.ko' -> '/mnt/hdd/workspace/mini_devices/friendlywrt23-rk3328/scripts/sd-fuse/out/output_rk3328_kmodules/
lib/modules/6.1.63/rtl8812au.ko'
depmod /mnt/hdd/workspace/mini_devices/friendlywrt23-rk3328/scripts/sd-fuse/out/output_rk3328_kmodules 6.1.63 ...
building kernel ok.
====Building kernel ok!====
$ cd kernel/drivers/net/wireguard
$ ls -l wireguard.ko
-rw-rw-r-- 1 chyi chyi 863608 June 12 14:55 wireguard.ko
=> Copy to target board.
root@192.168.2.1's password:
wireguard.ko 100% 843KB 14.4MB/s 00:00
b) Running it on NanoPi (1st test)
First, let's log in to NanoPi R2S Plus and proceed with the Wireguard setup.
$ ssh root@192.168.2.1
root@192.168.2.1's password:
___ _ _ _ __ __ _
| __| _(_)___ _ _ __| | |_ \ \ / / _| |_
| _| '_| / -_) ' \/ _` | | || \ \/\/ / '_| _|
|_||_| |_\___|_||_\__,_|_|\_, |\_/\_/|_| \__|
|__/
----------------------------------------------- ------
FriendlyWrt 23.05.3, r23809-234f1a2efa
------------------------------------ -----------------
📌 NanoPi R2S Plus has a console port (/dev/ttyUSB0, 1500000, 8N1) externally, so you can log in using that.
Linux nanobox-r2s-plus 6.1.63 #1 SMP Sun Apr 14 15:07:49 KST 2024 aarch64 GNU/Linux
=> Replace the currently running wireguard kernel module with l2 wireguard.
After rebooting, log in again and configure l2 wireguard settings as follows.
=> Generate curve25519 keypair.
=> You must specify l2wireguard to tunnel the entire ethernet frame.
=> Specify an IP for the wg1 interface. In the case of l3 wireguard, the IP for wgX means the vpn IP, but there is no need to specify it for l2 vpn. The reason for specifying the IP here is to do a ping test.
=> In the case of l2 wireguard, since it is an ethernet device, the MAC address must be specified.
=> Brings up the l2 wireguard interface.
FppVj8pZvJupnRI9admT8LPiXcwZ4eILHNhfUyU+XWk= allowed-ips 0.0.0.0/0 endpoint 192.168.8.125:51820
📌 Note 2) As mentioned above, allowed-ips must be set to 0.0.0.0/0 for normal operation.
📌 Note 3) Again, l2 wireguard must have a MAC address set.
Okay, now that all the basic settings are done, let's check it out. As expected, pinging to the peer vpn ip works fine. 😃
If you check the tcpdump result in this state, you can see that l2 wireguard is operating normally.

[Figure 3.8] L2 WireGuard normal operation verification(3) - raw packet capture
So far, we have installed the l2 wireguard kernel module on two NanoPis and verified that l2 wireguard is applied during 1:1 communication between NanoPis.
4. L2 WireGuard Operation Test #2
Well, but, the previous test is lacking by 2%. It is also difficult to tell what has changed compared to l3 wireguard. From now on, I will build the same environment as the one used to test SoftEther VPN mentioned in Chapter 1, and check if l2 wireguard operates normally in this state.
In reality, we need to test it in an Internet environment, but let's first conduct a test operation in a test environment like the one below.
First, let's set up the NanoPi R2S Plus.
# wg genkey | tee ./privatekey | wg pubkey > ./publickey
=> Generate curve25519 keypair.
=> You must specify l2wireguard to tunnel the entire ethernet frame.
FppVj8pZvJupnRI9admT8LPiXcwZ4eILHNhfUyU+XWk= allowed-ips 0.0.0.0/0 endpoint 192.168.8.125 :51820
=> Set device and peer settings. allowed-ips must be set to 0.0.0.0/0.
=> Set the MAC address for the wg1 interface. Each company has its own MAC address range, so let's utilize that.
=> Link up the wg1 interface.
# brctl delbr br-lan
=> Take down the previously configured br-lan bridge interface.
# ifconfig wg1 0.0.0.0
=> Remove the IP address of the interface to be included in the bridge. In the case of openwrt, eth1 is a LAN interface.
# brctl addif br-lan eth1
# brctl addif br-lan wg1
=> Create a new br-lan interface and include the eth1 and wg1 interfaces in the bridge.
=> Sets the address of the br-lan interface. Normally, the MAC address of eth1 is used as is.
=> This setting is actually unnecessary, so remove it.
=> Turns the bridge interface up.
#wg genkey | tee ./privatekey | wg pubkey > ./publickey
ip link add dev wg1 type l2wireguard
wg set wg1 listen-port 51820 private-key ./keys/privatekey peer FppVj8pZvJupnRI9admT8LPiXcwZ4eILHNhfUyU+XWk=
allowed-ips 0.0.0.0/0 endpoint 192.168.8.125:51820
ip link set dev wg1 address 02:ca:fe:f0:0e:04
ip link set wg1 up
ifconfig br-lan down
brctl delbr br-lan
ifconfig eth1 0.0.0.0
ifconfig wg1 0.0.0.0
brctl addbr br-lan
brctl addif br -lan eth1
brctl addif br-lan wg1
brctl setfd br-lan 1
brctl stp br-lan 1
ip link set dev br-lan address 56:97:4A:F7:7B:2E
ip link set br-lan up
Next, let's proceed with setting up the NanoPi R5C side.
# wg genkey | tee ./privatekey | wg pubkey > ./publickey
=> Generate curve25519 keypair.
=> You must specify l2wireguard to tunnel the entire ethernet frame.
=> Set the MAC address for the wg1 interface. Each company has its own MAC address range, so let's utilize that.
=> Link up the wg1 interface.
# brctl delbr br-lan
=> Take down the previously configured br-lan bridge interface.
# ifconfig wg1 0.0.0.0
=> Remove the IP address of the interface to be included in the bridge. In the case of openwrt, eth1 is a LAN interface.
# brctl addif br-lan eth1
# brctl addif br-lan wg1
=> Create a new br-lan interface and include the eth1 and wg1 interfaces in the bridge.
=> Sets the address of the br-lan interface. Normally, the MAC address of eth1 is used as is.
=> You need to set it like this for remote dhcp to work properly (maintain existing settings).
=> Turns the bridge interface up.
#wg genkey | tee ./privatekey | wg pubkey > ./publickey
ip link add dev wg1 type l2wireguard
wg set wg1 listen-port 51820 private-key ./keys/privatekey peer jkOW74X1CRS8fobzmYYPGDkyVhR5rd
ip link set dev wg1 address 02:ca:fe:f0:0e:05
ip link set wg1 up
ifconfig br-lan down
brctl delbr br-lan
ifconfig eth1 0.0.0.0
ifconfig wg1 0.0.0.0
brctl addbr br -lan
brctl addif br-lan eth1
brctl addif br-lan wg1
brctl setfd br-lan 1
brctl stp br-lan 1
ip link set dev br-lan address 1E:45:77:76:DE:26
ip address add dev br-lan 192.168.3.1/24
ip link set br-lan up
With the L2 wireguard tunnel created, manually change the IP settings of the Linux notebook (on the left) as shown below.
Oh, but up to this point, I thought everything was working perfectly in the test, but there was one big problem. That is, ping to the internet, dns, etc. are working fine, but web, ssh, ftp, etc. are not working well. Why is that?
<NanoPi R5C>
# tcpdump -i eth0
21:45:56.547525 ARP, Request who-has 112.175.235.196 tell 192.168.8.182 , length 46
__________________________________________________________________________
Looking at the content, it is asking 192.168.8.182, i.e. NanoPi R2S Plus (wan IP), to tell the MAC address of 112.175.235.196 (web server). If it were not an L2 VPN situation, Gl.iNet MT1300 would have immediately sent an ARP reply.
(No L2 VPN situation) Linux Notebook -> NanoPi R2S Plus(wan: 192.168.8.182) -> Gl-iNet MT1300
However, in the L2 VPN situation, the ARP Reply does not go to the NanoPi R2S Plus via the L2 Wireguard as shown in the figure below, but rather the response goes directly ( B - ARP Reply ). Therefore, in this case, if the NanoPi R5C in the middle acts as an ARP proxy (instead, sends an ARP reply with its own MAC address), the problem can be solved ( C - ARP Reply ).
_______________________________________________________________
For reference, if you use L2 WireGuard, the following basic network configuration is possible. You can enjoy the same effect as if you were connecting a very long LAN cable from your home to your office.
If you use L2 WireGuard, you can also create a VPN configuration that operates (standalone server) without changing the office network configuration (right side of the figure below).
Above, I analyzed the source code of L2 WireGuard implemented by Fadis (NAOMASA MATSUBAYASHI) and introduced the actual operation process in the NanoPi environment. L2 WireGuard is pretty great~ 😍
5. Creating L2 VPN with GRETAP + L3 WireGuard
In this chapter, I will briefly introduce how to create an L2 VPN by combining GRE Tunnel and WireGuard. It would also be interesting to compare the differences with L2 WireGuard, which was explained in the previous chapter. 👌
- Implementing Layer 2 VPN using GRETAP over L3 WireGuard
- See the site below
https://gist.github.com/zOrg1331/a2a7ffb3cfe3b3b821d45d6af00cb8f6
https://notes.superlogical.ch/pages/note_wg/nolayer2/
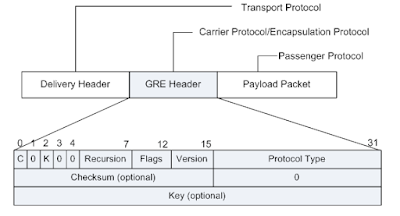
📌 The GRE header is usually 4 bytes, and optional fields can be added.
Since the background explanation has already been sufficiently provided in the previous chapter, only the setup method and test results will be mentioned here.
(Of course) before the test, wireguard.ko must be replaced with the original version (l3 wireguard) and then the test must be conducted.
<Test environment>
First, let's proceed with setting up the NanoPi R2S Plus (Client side).
# wg genkey | tee ./privatekey | wg pubkey > ./publickey
# ip link add dev wg0 type wireguard
# ip address add dev wg0 10.1.1.1/24
# ip link set wg0 mtu 1402 up
# wg set wg0 listen-port 51820 private-key ./keys/privatekey peer FppVj8pZvJupnRI9admT8LPiXcwZ4eILHNhfUyU+XWk= allowed-ips 0.0.0.0/0 endpoint 192.168.8.125:51820
# ip link add name gretap1 type gretap local 10.1.1.1 remote 10.1.1.2
# ip link set gretap1 up
# ifconfig br-lan down
# brctl delbr br-lan
# ifconfig eth1 0.0.0.0
# brctl addbr br-lan
# brctl addif br -lan eth1
# brctl addif br-lan gretap1
# brctl setfd br-lan 1
# brctl stp br-lan 1
# ip link set br-lan up
Next, let's proceed with setting up the NanoPi R5C side (server side).
# ip link add dev wg0 type wireguard
# ip address add dev wg0 10.1.1.2/24
# ip link set wg0 mtu 1402 up
# wg set wg0 listen-port 51820 private-key ./keys/privatekey peer jkOW74X1CRS8fobzmYYPGDkyVhR5rdEa9uh8QA2O/0k= allowed-ips 0.0.0.0/0 endpoint 192.168.8.182:51820
# ip link add name gretap1 type gretap local 10.1.1.2 remote 10.1.1.1
# ip link set gretap1 up
# brctl delbr br-lan
# ifconfig eth1 0.0.0.0
# brctl addbr br-lan
# brctl addif br-lan eth1
# brctl addif br-lan gretap1
# brctl setfd br-lan 1
# brctl stp br-lan 1
# ip address add dev br-lan 192.168.3.1/24
# ip link set br-lan up
# echo 1 > /proc/sys/net/ipv4/conf/br-lan/proxy_arp
📌 Although it was not specifically mentioned when explaining L2 WireGuard, both L2 WireGuard and GRETAP + WireGuard may require TCPMSS settings if necessary.
iptables -A FORWARD -p tcp --tcp-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtu
Oh, it's better than I thought. The speed doesn't seem that slow either... Hmm, this method is quite useful, too. 😁
6. The story that hasn't been told yet
1) Apply L2 WireGuard between Client and Server located in the same LAN
- A situation where you want to communicate encrypted between two machines on the same LAN without changing IP settings.
- How to solve loop problem? Is it possible?
2) Applying PQC Algorithm(CRYSTALS Kyber KEM) to L2 WireGuard
- As briefly introduced in a previous blog post, let's try applying CRYSTALS Kyber KEM to L2 WireGuard.
https://slowbootkernelhacks.blogspot.com/2023/02/nanopi-r4s-pq-wireguard-vpn-router-part.html
3) Applying L2 WireGuard to wireguard-go code
- Let's apply l2 wireguard to wireguard-go code for userspace.
4) Connecting L2 WireGuard and FD.io VPP
- Let's connect VPP and L2 WireGuard using the tap interface.
- Wouldn't that be possible?
To be continued...
________________________________________________________
WireGuard® is a registered trademark of Jason A. Donenfeld.
May The Source Be With You
7. References
[3] https://speakerdeck.com /fadis/zuo-tuteli-jie-suruwireguard
[4] https://slowbootkernelhacks.blogspot.com/2023/02/nanopi-r4s-pq-wireguard-vpn-router.html
[5] https://slowbootkernelhacks.blogspot.com/2020/09/wireguard-vpn.html
[6] https://www.softether.org/
[7] my blog post that is related to wireguard
[7.1] https://slowbootkernelhacks.blogspot.com/2020/04/espressobin-wireguard-vpn.html
[7.2] https://slowbootkernelhacks.blogspot.com/2020/05/openwrt-gainstrong-minibox3-wireguard.html
[7.3] https://slowbootkernelhacks.blogspot.com/2020/09/wireguard-vpn.html
[7.4] https://slowbootkernelhacks.blogspot.com/2023/01/orangepi-r1-plus-lts-pqc-wireguard-vpn. html
[7.5] https://slowbootkernelhacks.blogspot.com/2023/02/esp32-wireguard-nat-router-pqc.html
[7.6] https://slowbootkernelhacks.blogspot.com/2023/02/nanopi-r4s-pq-wireguard-vpn-router-part.html
[7.7] https://slowbootkernelhacks.blogspot.com/2023/02/nanopi-r4s-pq-wireguard-vpn-router.html
[7.8] https://slowbootkernelhacks.blogspot.com/2024/01/dpdk-fdio-vpp-security-gateway.html
[7.9] https://slowbootkernelhacks.blogspot.com/2024/05/nanopi-wireguard-go-quantum-safe-vpn.html
[8] https://gist.github.com/zOrg1331/a2a7ffb3cfe3b3b821d45d6af00cb8f6
[10] https://www.netmanias.com/ko/post/blog/5348/dhcp-ip-allocation-network-protocol/understanding-the-basic-operations-of-dhcp
[11] https://info.support. huawei.com/info-finder/encyclopedia/en/GRE.html
[13] And Google~
Slowboot


.jpg)




































.png)








댓글 없음:
댓글 쓰기